The second post in my series as I share my learnings with AWS Network Firewall.
If you want to start at the beginning, check out part 1 here
Let's get into setting up an Inspection VPC!
The Setup
To build our example, we start with the following.
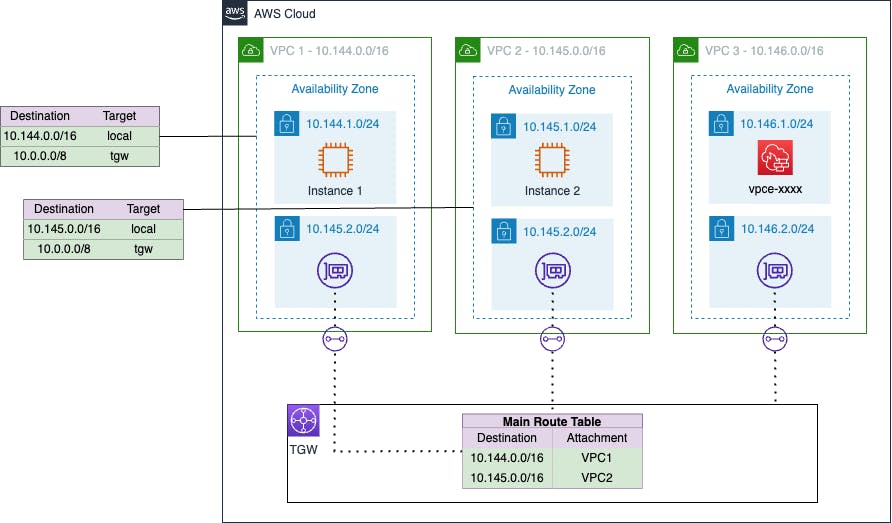
All VPCs are attached to the TGW and use a single availability zone.
VPC 1 & 2 host our client instances, and VPC 3 is our inspection VPC with the firewall instance.
All of the VPCs have a TGW subnet, which hosts the attachment interface for the TGW.
VPCs 1 & 2 have a straightforward route table passing anything that isn't part of the local VPC CIDR to the TGW.
The TGW Main Route Table passes traffic to the relevant VPC based on the destination CIDR. The use of propagated entries here makes management effortless.
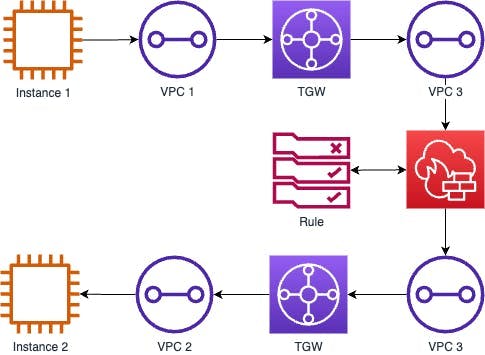
If instance 1 were to communicate with instance 2, the flow would be as follows:-
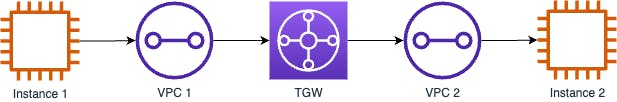
Now let's put the Inspection VPC in the mix!
Inspection VPC
To pass traffic to the firewall, we need to update the TGW Route Table associations:-
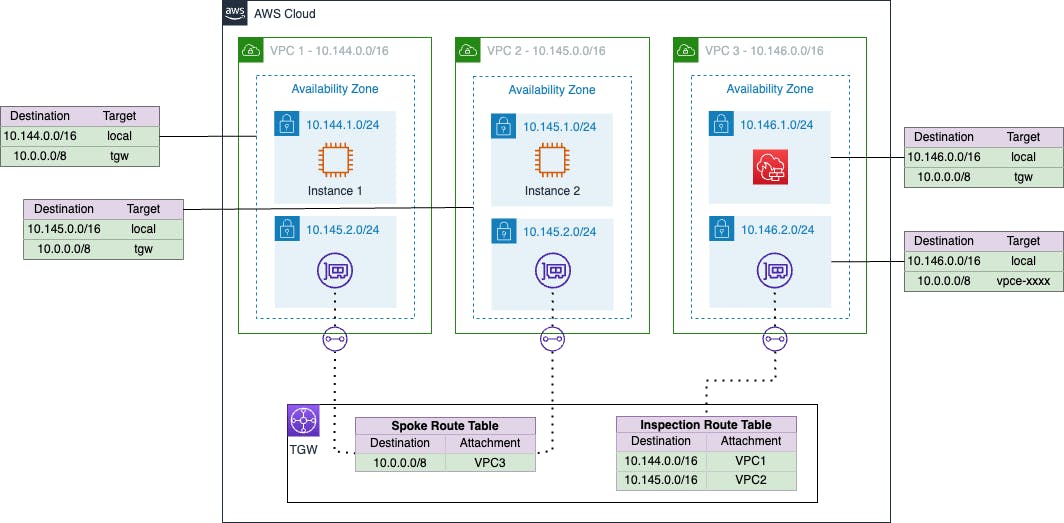
Spoke Route Table & Association with VPC 1 & 2
With this configuration in place, any traffic received from the attached VPCs destined for 10.0.0.0/8 is passed to the firewall for processing.
Using 10.0.0.0/8 covers anything outside the local VPC CIDR while keeping the spoke route table friendly and straightforward.
It's important to note that spoke route table entries will be manually added. We can't use propagation as it would bypass the firewall and go direct to the relevant attachment.
Inspection Route Table & Association with VPC 3
Once the firewall has processed traffic, it must be passed to the correct VPC attachment. The Inspection route table needs entries for all the VPCs that will pass traffic to it for processing.
The Inspection route table can benefit from route propagation, so we don't have to manually update it as additional CIDRs are added to VPCs 1 & 2.
Inspection VPC Route Table Configuration
When traffic is passed to the Inspection VPC attachment, it flows as follows:-
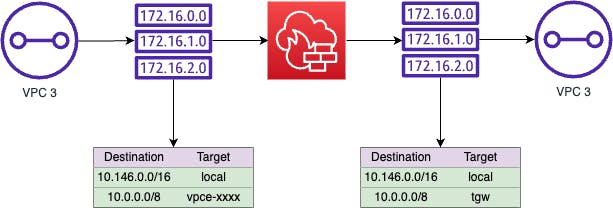
- The TGW delivers traffic to the attachment
- The TGW subnet route table passes the traffic to the firewall
- The Firewall processes the traffic
- The Firewall subnet route table passes the traffic to TGW
Now when instance 1 communicates with instance 2, the flow would be as follows if there was a rule allowing it!
Summary
Adding the Inspection VPC is about controlling the routing configuration within Transit Gateway and the correct flow within the Inspection VPC itself.
In part 3, we will expand on this example and see what things look like as we introduce multiple availability zones.
I hope this helps someone else!
Cheers

